This time, I received a request to analyze log files to find the cause of an attack on a company’s website using WordPress. Website was attacked by hackers and data was deleted.
Below is an image of “one corner” of the log file.
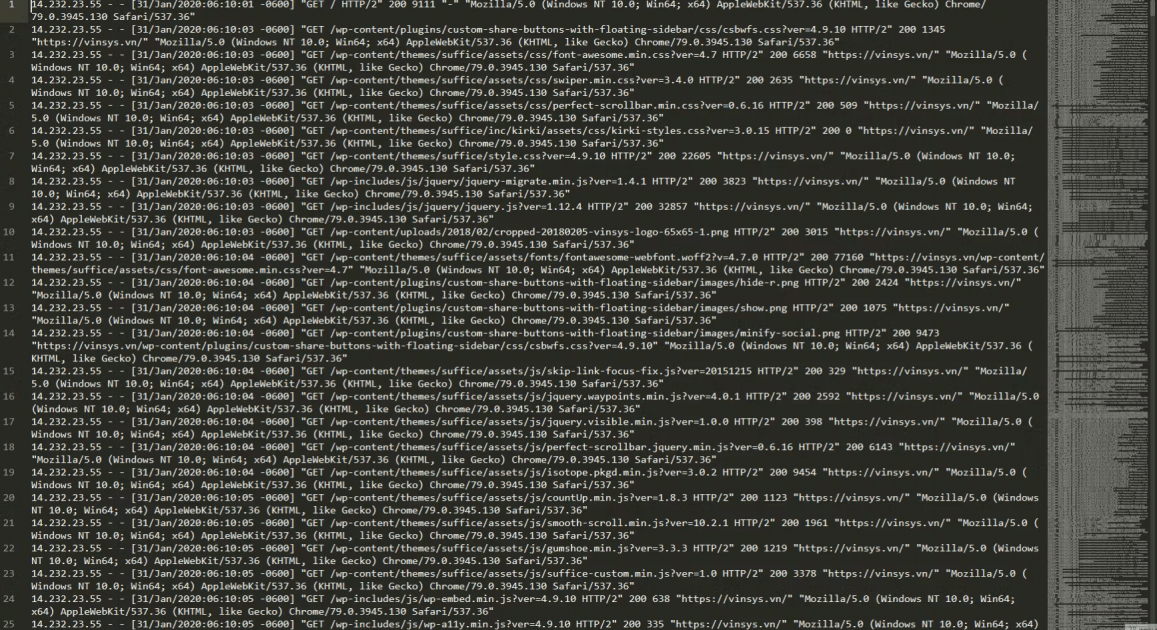
In this investigation, I used SublimeText 3 and Google :v Initially, I read through the entire log file several times to grasp the structure of the file’s content. In general, this log file is not long (about 4500 lines), so I can easily grasp it. After reading through it a few times, I noted a few requests that were “different” from the rest. In addition to requests from bots and requests to read website articles, I have listed a few signs (in my opinion, they are suspicious). However, after searching Google for a while, those signs don’t say much. I started thinking that if the website had its entire database deleted, there would be some action related to “admin”, Ctrl + F and start searching.
Oh, a pretty interesting line as shown below (maybe because I missed this detail when I read the log):
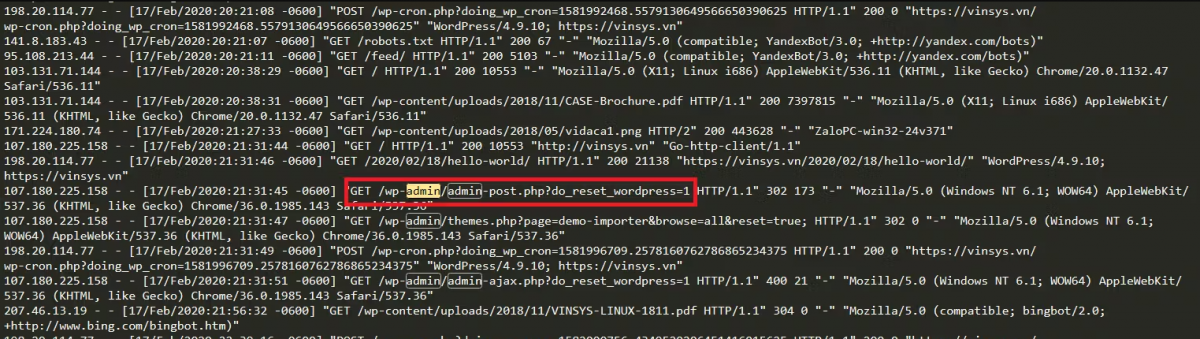
At this point, I continued to google about the above request and discovered that this was a malicious request targeting a vulnerability in a WordPress plugin called “ThemeGrill Demo Importer”. This vulnerability allows attackers to delete all tables in WordPress.
Request: “GET /wp-admin/admin-ajax.php?do_reset_wordpress=1 HTTP/1.1”
More information about the vulnerability: By sending a call to /wp-admin/admin-ajax.php?action=anything&do_reset_wordpress=1, the database will be wiped and we will be logged in as “admin” if the “admin” user exists in the users table. Authentication is not required.
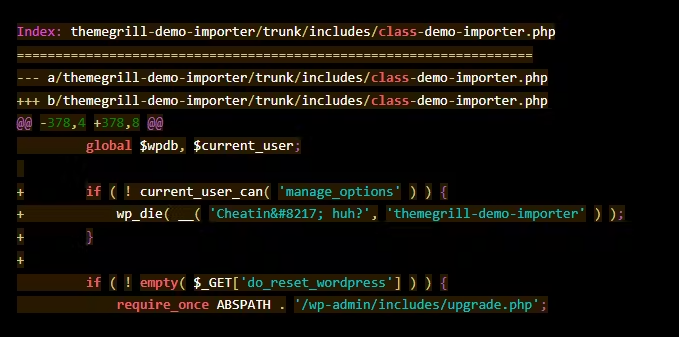
From the above information along with the fact that all articles on the Website were deleted, it can be concluded: The cause of the attack was because the Website used a vulnerable version of the ThemeGrill Demo Importer plugin. Hackers take advantage of vulnerabilities in this plugin to send malicious requests to delete website posts. Below is information about the patch (version 1.6.2):
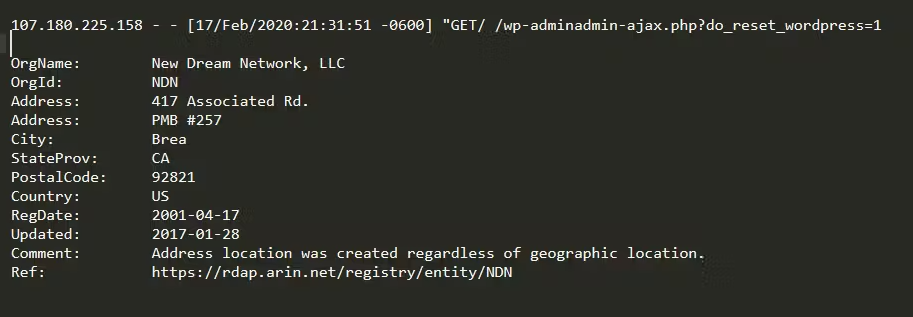
Additionally, the source IP address of the attack on this website (107.180.225.158) was also shared on the internet, which means hackers exploited this vulnerability on many WordPress websites using the ThemeGrill Demo Importer plugin ( mid-2020).

Solution:
Block the source IP addresses of the attack and update the ThemeGrill Demo Importer plugin to the latest version.
Author: Hoang Duc Hoan – VSEC





















